Digital Workplace Partner That You Can Trust
IT Outsourcing that won’t cost you peace of mind. At BitSys Technologies, we believe in working as partner not a vendor. With over 15 years of outsourcing experience, we know the key to great IT service.
01.
▷
The Metaverse is rising rapidly.
Is this the highest evolution of the human-machine experience?
02.
▷
Is Mac the future of enterprise?
A discussion about the exceptional adoption rate of Mac devices in Enterprise.
03.
▷
The Work from Anywhere world.
How to ensure security & employee satisfaction without compromise?
BLOGS
INSIGHTS
Approach
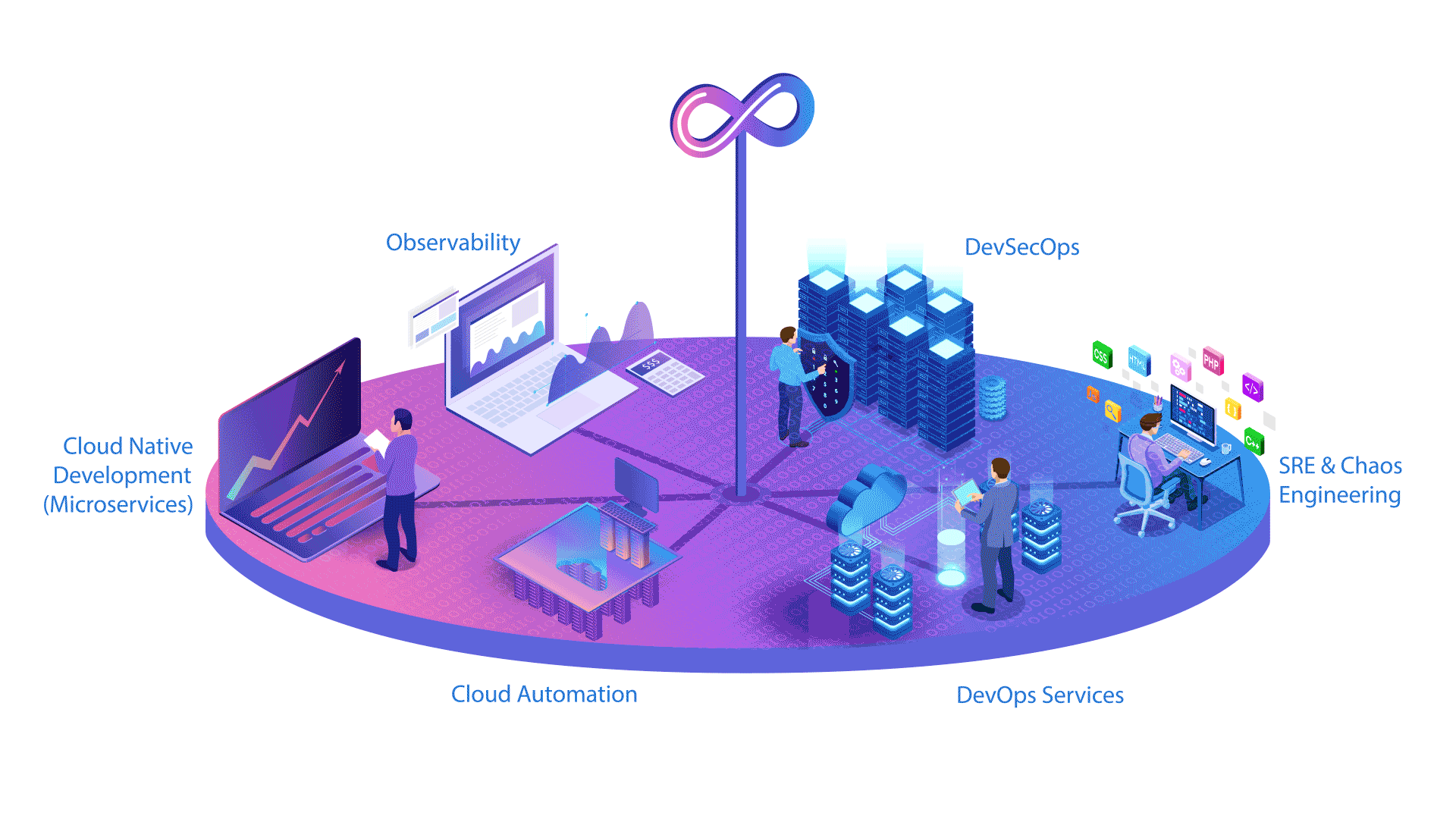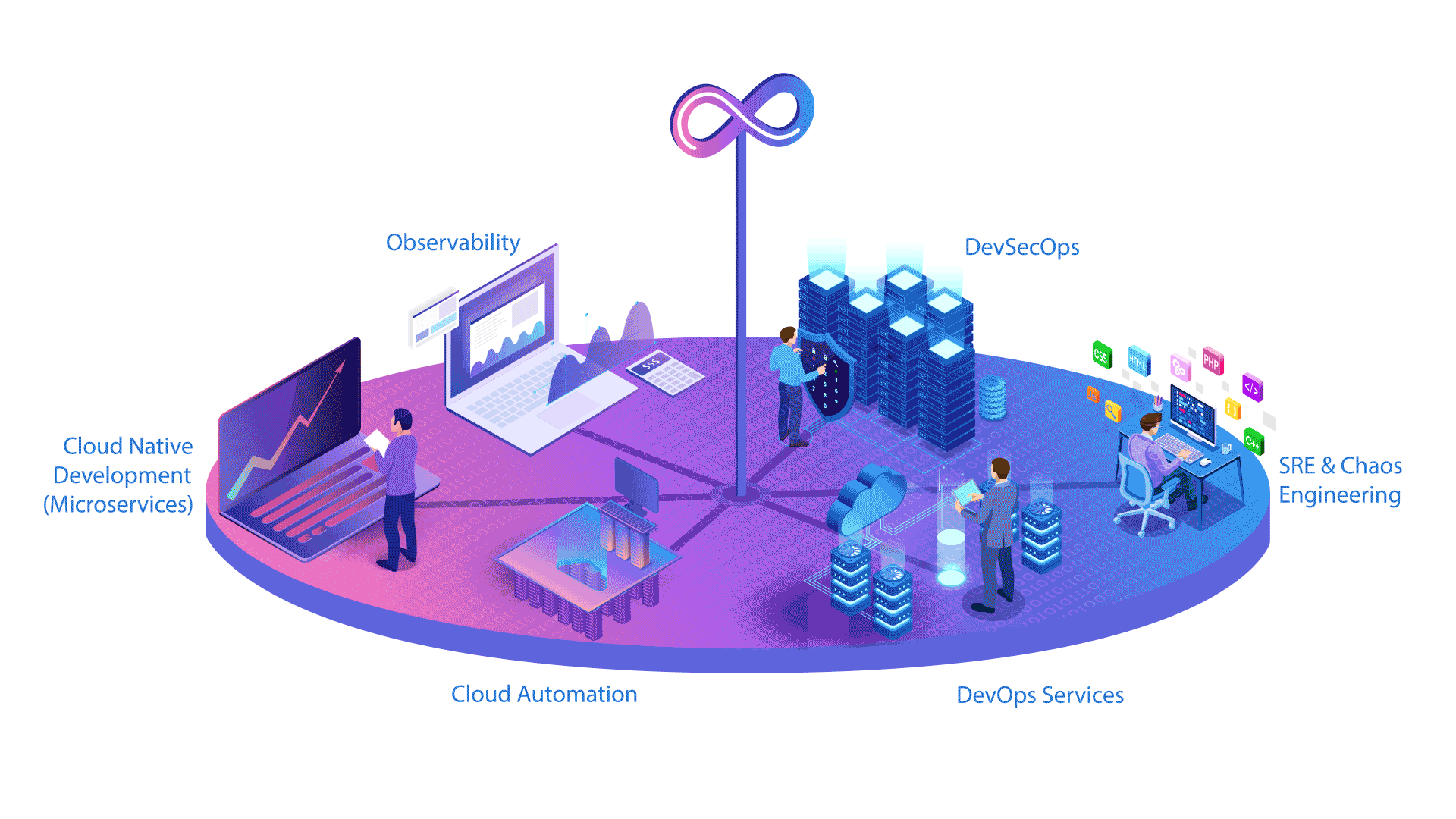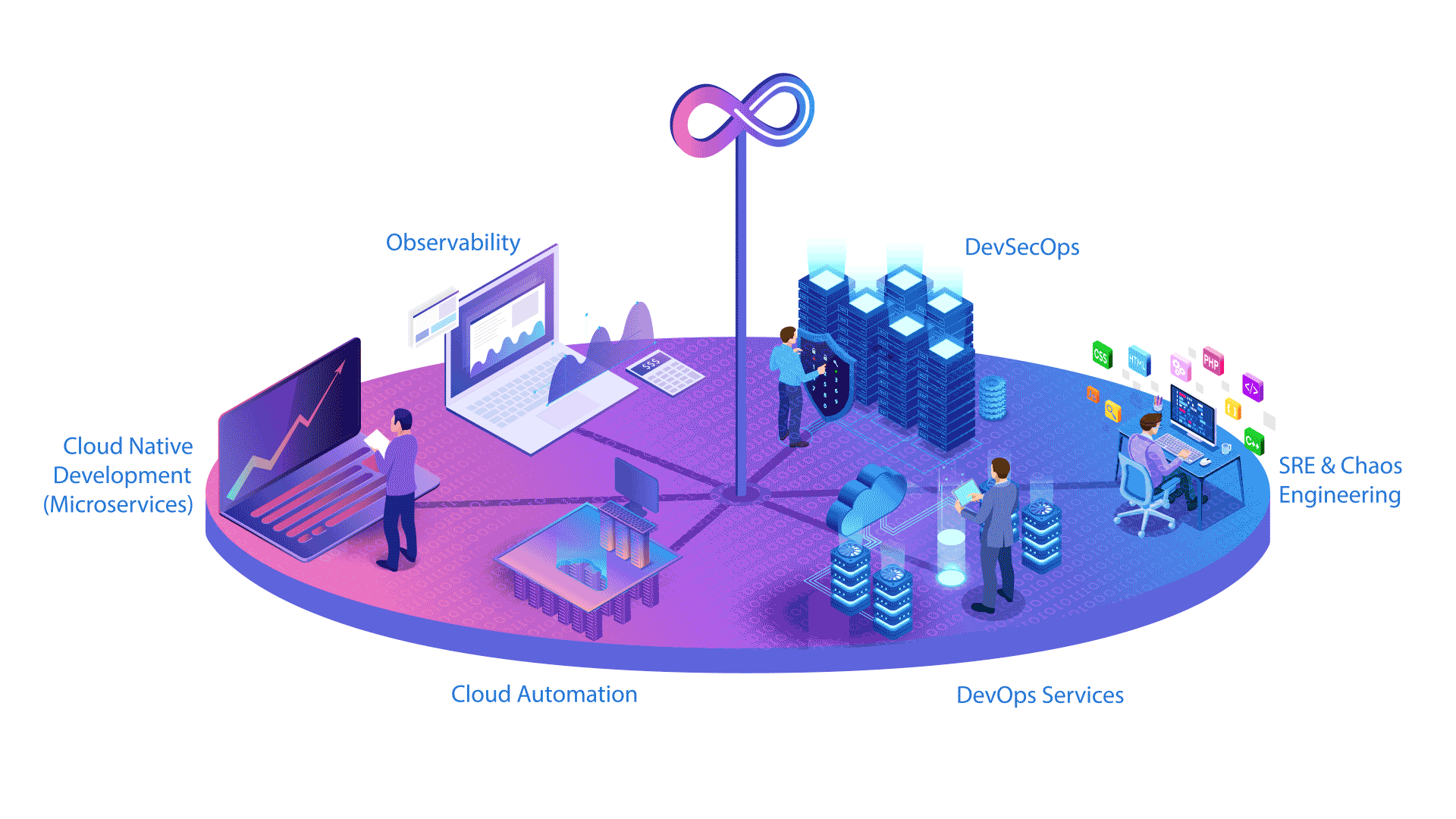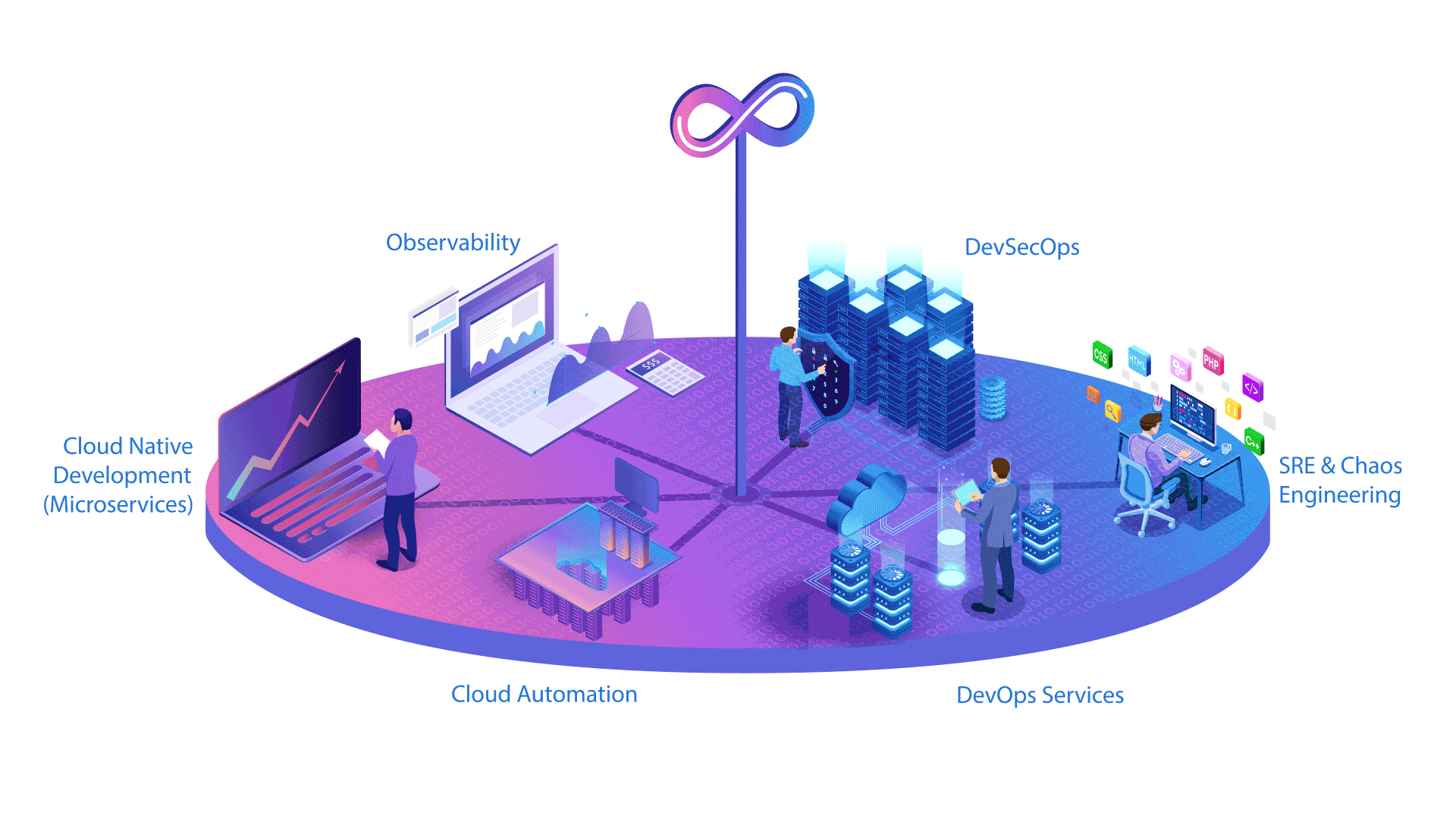
DevOps・Agile
Traditional outsourcing companies focus on delivering the services that are in the contract. We, at BitSys Technologies, aim towards continuous service improvement by implementing DevOps, Automation via Scripting & ensuring that Agile is improving the overall delivery of services.
Implementing Machine Learning in IT Support Setup
Machine learning has the potential to revolutionize the way IT support businesses operate. This cutting-edge technology can be applied in a number of ways to improve the efficiency, accuracy, and speed of IT support services. Here are some ways that machine learning can be used to enhance IT support services: In conclusion, machine learning has […]
Adoption of Macs in Enterprise: A Growing Trend
This image belongs to Kandji.io In recent years, there has been a growing trend of enterprises adopting Macs as their primary desktop and laptop computers. This shift in technology can be attributed to several factors, including the increasing popularity of Macs among employees and the growing number of enterprise-level software solutions available for Macs. One of the main reasons for the growing adoption of Macs in enterprises is the increasing popularity of Macs among employees. Many employees prefer Macs due to their sleek design and user-friendly interface. Additionally, Macs are known for their durability and reliability, which is essential for employees who rely on their computers for work. Another reason for the growing adoption of Macs in the enterprise is the increasing number of enterprise-level software solutions available for Macs. In the past, Macs were not seen as a viable option for enterprise use due to a lack of software options. However, with the increasing popularity of Macs, many software providers have developed enterprise-level solutions for Macs, including enterprise resource planning (ERP) systems, customer relationship management (CRM) software, and more. While the adoption of Macs in the enterprise has its benefits, there are also some challenges that need to be…
Secure Your Mac with FileVault
FileVault is a built-in encryption tool for Macs that helps protect your data from unauthorized access by encrypting your hard drive. Enabling FileVault is a simple process that only takes a few minutes, and it can give you peace of mind knowing that your data is safe and secure. In this blog post, we will […]
Cost saving for enterprises by choosing M1 Macs
The M1 Mac has had a significant impact on the enterprise market since its release. As a highly-efficient and powerful machine, the M1 Mac has proven to be a valuable asset to businesses in a variety of industries. One of the key benefits of the M1 Mac is its improved performance. The M1 chip, which […]
What questions should you ask before signing up for NOC services
1. Where is the NOC situated, and who is in charge of it? Enquire specifically about the location of the NOC. It has been common practise among NOC providers supporting MSPs to hide the fact because the NOC is not located in the same geographic area as their headquarters. Additionally, ensure that the NOC is […]
Why Penetration testing is important?
Penetration testing (also known as pen testing or ethical hacking) is a security procedure that involves analyzing your computer system’s software for vulnerabilities and susceptibility to attacks such as hacking and cyber-attacks. Software faults, design errors, and configuration problems are all examples of vulnerabilities. To ensure that Information Technology (IT) infrastructure remains powerful and well-protected, […]
What is NOC and Advantage of NOC Services
A NOC, or Network Operations Center, is a centralized facility where IT support technicians control, monitor, and maintain customer connections. The overall goal of a NOC is to keep the network going smoothly and without interruptions. The NOC Services provides data security for network quality 24 hours a day, seven days a week, to assist, […]
What Every CISO Must Know For 2023? | Cyber Security Best Practices
There is no shortage of challenges facing chief information security officers (CISOs). Expanding sources of attacks and complex cloud security environments have created new advanced threats. Regulations regarding compliance have become more stringent and punitive. And while digital transformation promotes business pace, its impact is often limited by budget constraints and gaps in security talent. […]
Future Of Cybersecurity: 4 Evolving Technologies
More than ever, we conduct more of our personal lives and business activities online, making cybersecurity a key issue of our time. Understanding what cybersecurity’s future it – will teach you how to make the best use of your resources and remain secure not only today but tomorrow as well. The future of cybersecurity is […]
Cyber Security Trends 2023
Cyber security is like the chessboard where hackers are searching to checkmate the defenders. Hackers are outplaying the defenders by launching an attack every 39 seconds. Cases of cyberattacks are increasing and these cybercriminals have become more creative by finding new ways to exploit the users and technology to access passwords, networks, and also valuable […]
Blackbaud Hack – One More Ransomware Attack
Hackers are getting smarter day by day. Every day we are hearing the news on breaches or cyberattacks on a small scale or a mass scale. Last month we have heard of the Twitter attack and this time it’s a ransomware attack on Blackbaud, a US-based company – the largest provider of CRM. Blackbaud is […]
Trojan Vs Virus Vs Worm | What Is The Difference?
If the subject of a computer virus comes up, the most popular blunder people do is to refer to a worm or trojan horse as a virus. Although the terms Trojan, worm and virus are often used interchangeably, they are not similar. Viruses, worms, and trojan horses are all malicious programs that can damage your […]
What Are Rootkits-How To Identify Them
Rootkits are amongst the easiest to detect and disable Malware. Now Windows 10 systems are aimed at different variants. What is a Rootkit? Rootkits are the world of malware toolboxes. They are installed as part of some other update, backdoor, or worm. They then take action to ensure that the owner will not sense their […]
Internal Ransomware Attack And How To Prevent It ?
Ransomware attacks are growing each day. There are many reasons for an internal ransomware attack. Cybercriminals have been creating various methods to lure their victim. One of the main methods they use for ransomware is phishing emails. With an intention of extortion, ransomware is a form of malware that targets your critical data and systems […]
Network Defence As Service
To protect organisations from cyber threats, network defence management is important. Network Defence as a Service helps to identify, detect, and respond to threats to your network easily and effectively without needing any additional hardware, software, or people. By using computer network defence methodologies and resources to address technological and functional customer-based problems, the BitSys […]
What Is A Hybrid Workforce And How To Secure Them?
Companies are gradually embracing a hybrid workforce model across a variety of industries: AI (Artificial Intelligence)-powered digital colleagues work alongside their human counterparts and assist them. The global transition to a remote workforce has redefined the way business models are organized by companies. A new age of work will arise as executives revive work policies […]
7 Different Types of Cyber Security Threats
Cyber security experts should be well-versed in the following kinds of cyber security threats. 1. Viruses Malware, which covers keyloggers, ransomware, infections, and bugs, is defined as malicious software. Malware is started when a people click on a phishing email or file, which results in dangerous software getting installed. According to Cisco, once activated, malware […]
By 2025
BitSys Technologies is set to be a
Carbon Neutral Company.